BACKGROUND
Controller Area Network (CAN) is the dominant network architecture used to connect Electronic Control Units (ECU) across virtually all makes and models of vehicles today. CAN is a broadcast messaging protocol where messages transmitted by one node are received by all network nodes. An interconnected node on a CAN bus may communicate with any other node because CAN lacks common message authentication capabilities. Compromised nodes on a CAN bus may send malicious messages to other nodes that contain inaccurate status or bogus control messages that could affect the safety of the driver. The purpose of this research was to address CAN bus security issues, where we evaluated a technique that can not only detect cyber-attacks on a CAN bus but also adapt the system to remove malicious messages.
APPROACH
To address security issues on CAN, we added a secondary bus for malicious nodes. When malicious packets are detected, the suspected node is transferred to the secondary bus. Packets from the primary bus are replayed onto the secondary bus where packets from the secondary bus will be filtered to remove malicious packets before replaying them on the primary bus.
ACCOMPLISHMENTS
Before this Quick-Look (QL) Internal Research and Development (IR&D), we had developed a desktop program capable of monitoring a CAN bus and detecting malicious packets. For this project, the software was recompiled into a Dynamic Link Library (DLL), an Application Program Interface (API) was added, and a function to automatically load CAN bus training data was developed. We ran into an issue interfacing this program to the CRIO controller. To address the issue, a patch was implemented using a buffer to hold packets until the detection algorithm read the buffer. This worked well, but dramatically increased Field Programmable Gate Array (FPGA) compile time and severely limited the available resources for other tasks. Although the patch works, it is a sub-optimal solution and still drops a small number of packets. For the follow-on proposal, we plan to use the most powerful FPGA hardware available for CRIO and the software will be structured in a more efficient manner per guidance provided by National Instruments. The on-vehicle implementation is shown in Figure 1. This research allowed us to respond to the customer’s request for information for an Intrusion Defense System (IDS) that required a demonstrated benchtop system.
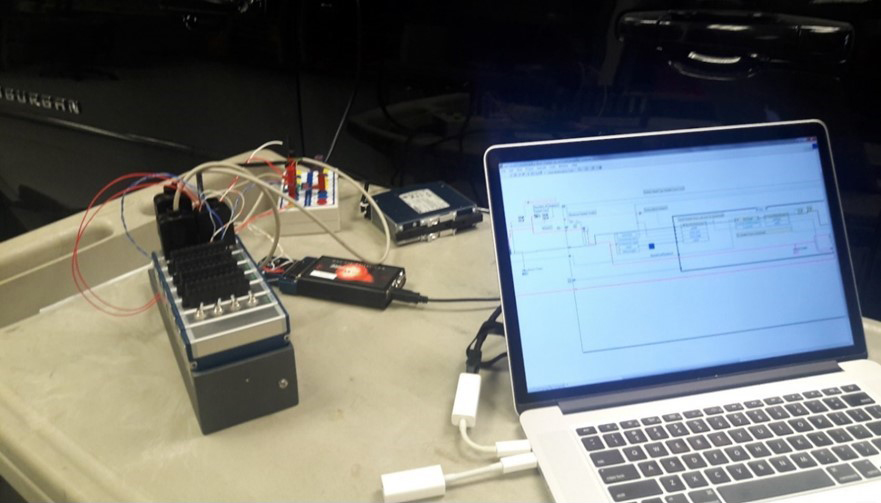
Figure 1: Intrusion Defense System Connected to SUV
