Background
Industrial control systems (ICS) networks have historically been overlooked in the realm of cybersecurity. Traditionally, these networks have been kept separate from information technology (IT) networks, which provides a simple and impenetrable cyber-security barrier. This “air-gap,” combined with the uptime requirements of most ICS networks, results in few firmware or software upgrades for devices on the network. As modern business practices require more insight into manufacturing processes, ICS networks are connected to IT networks, which exposes the ICS devices to the Internet-based attacks from which they were historically protected. Furthermore, the need for uptime and the slow rate of vendor security updates requires external methods of mitigation for these attacks.
SwRI has an established history of developing intrusion detection systems (IDS) for automotive networks, which share many characteristics with ICS networks. The primary objective of this research is to determine if the algorithms developed for automotive IDS applications could be leveraged into ICS applications, more specifically on an ICS network protocol such as Modbus/TCP.
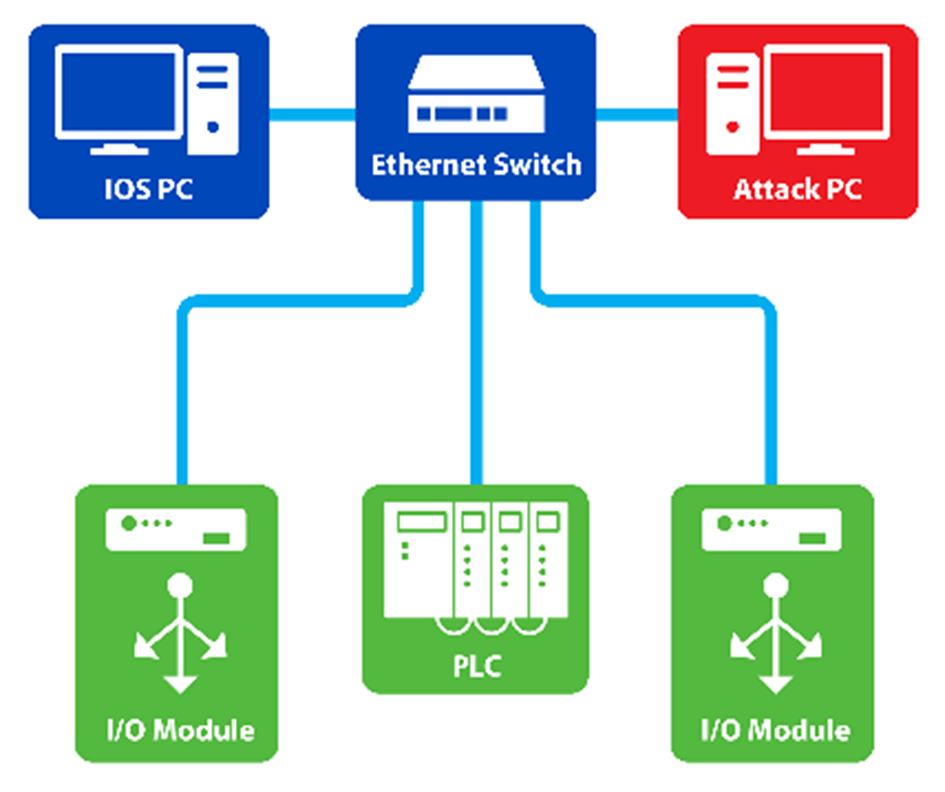
Figure 1: Compromised ICS Network Diagram.
Approach
SwRI developed algorithms to detect three potential types of attacks: out-of-band timing (packets not arriving at an expected time), address probing (packets requesting addresses outside the expected range), and data fuzzing (packets showing data out of the expected range). An IDS was then applied to pre-recorded Modbus data from an actual ICS network as well as from a test network where attacks of all three types were simulated. The resulting detections from the IDS application were then compared to the actual attacks performed against the network to determine the efficacy of the detection algorithms.
Accomplishments
The IDS system SwRI developed was able to detect all three attack types with a true positive rate (TPR) of 100% and a false positive rate of under 1%. These rates were accomplished using concepts not used in previous IDS applications, such as multi-modal distributions. These new concepts are now included in the toolset SwRI can provide to clients needing IDS capabilities.
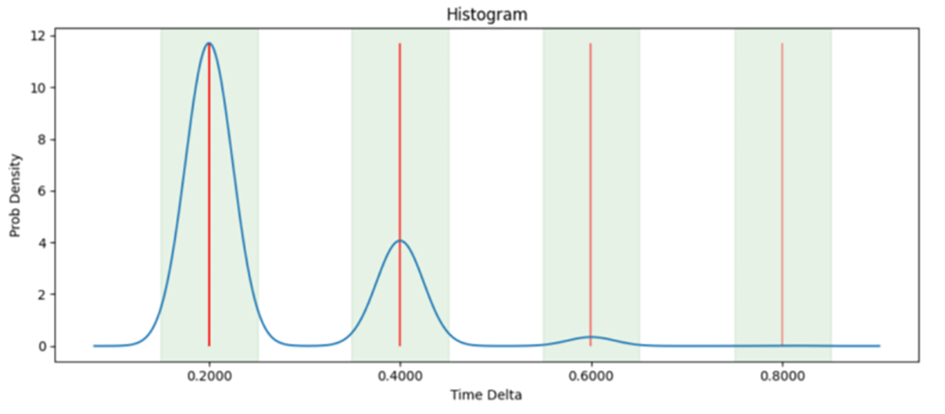
Figure 2: TCP Timing Probability Distribution
