Submitted by Austin Dodson on Fri, 05/20/2022
Industrial robotics continue to rise in levels of autonomy, intelligence and complexity, which enables them to fill more roles within the manufacturing process. However, as those systems rise in their independence, the need to ensure they are secure against cyberattacks has risen accordingly. Identifying the risks to robotics systems and corresponding solutions will help prevent costly cyberattacks to industrial control systems in the future.
Threats to Industrial Robot Networks
Industrial control systems are increasingly connecting remotely and becoming software dependent, exposing new vulnerabilities in systems that formerly required physical access to attack. As a result, a variety of different malware that target weaknesses in robotics systems have been developed. The illustration below indicates where vulnerabilities can occur in an industrial network in which computers and hardware share data across several operational zones.
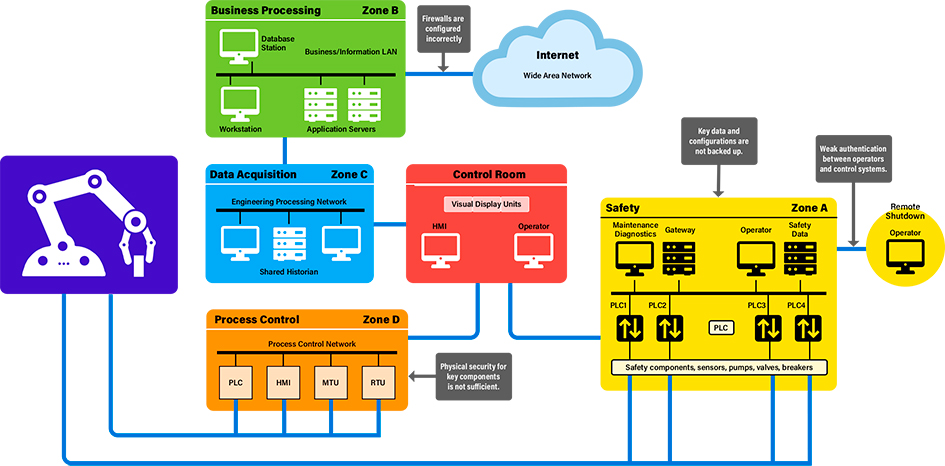
Cyber threats can occur through a failure to back up data and configurations (Zone A), incorrect firewall configuration and weak authentication between operators and control systems (Zone B), incorrect configuration of firewalls and insufficient physical security to hardware (Zone D).
These attacks take advantage of weaknesses often found in industrial systems, such as a lack of strong passwords and an abundance of default accounts that allow for easy compromise. Such weaknesses in authentication policies ensure that once an attacker has access to a robot, they will eventually be able to gain the authorization to control them. Robotics systems, however, typically rely on perimeter defenses to prevent unauthorized access to their networks and often neglect defense in-depth strategies that decrease the likelihood of a successful attack.
Patching is a key part of the software development cycle. Despite best efforts during development, new techniques will inevitably reveal vulnerabilities in published software, so the ability to update the software to eliminate these new threats is crucial. However, that task becomes more difficult in industrial settings where shutting down a system to deploy an update can result in significant lost revenue while an assembly line sits dormant. Thus, manufacturing technology is often not updated when it needs to be. Parts that have been proven to be reliable are prioritized over newer parts that, while more secure, would require downtime to be installed. These reliable parts may function well from a production standpoint; however, the potential costs of a security incident such as a ransomware attack caused by vulnerable technology need to be considered.
There are a variety of examples of these types of attacks. One of the most well-known was the attack against Iranian centrifuges in 2010 by the Stuxnet virus. This was one of the first examples of an attacker demonstrating advanced knowledge to target an industrial control system (ICS). Using knowledge of supervisory controls and data acquisition (SCADA) systems, the attacker was able to change the speed of the motors to cause physical damage to the centrifuges. Another example is the attack carried out against a German steel plant in 2014. Attackers were able to use a phishing attack to gain access to the network that controlled a blast furnace. Once they had access to the network, they were able to control the system, shut down the production facilities and cause damage to the equipment.
Industrial Control Systems Cyber Security
To help government and industry detect such threats, SwRI is developing algorithms that serve as an intrusion detection system (IDS) for industrial control systems (ICS). SwRI researchers demonstrated vulnerabilities in a test SCADA network featuring industrial control systems (ICS) that utilize the Modbus/TCP Ethernet-based networking protocol. This type of configuration is common in SCADA systems that utilize programmable logic controllers (PLCs) and input/out (I/O) modules in manufacturing robotics or utility applications. Learn more about the network here.
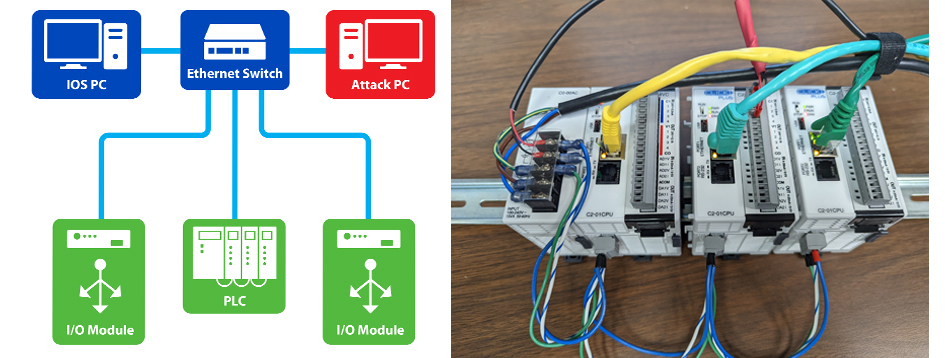
A test network, left, featured PLCs and I/O modules (right). Algorithms scanned the network for cyber threats such as out-of-band timing, address probing and data fuzzing/manipulation.
Industrial Robotics Security Best Practices
The National Institute of Standards and Technology (NIST) provides guidance on securing robotics systems, including the NIST 800-82 Guide to Industrial Control Systems (ICS) Security. This document acknowledges that industrial systems have different priorities than enterprise networks. When prioritizing security measures, availability is much more important than confidentiality and integrity. It provides guidance on how to analyze risk properly in an industrial setting as well as how to architect a network in a secure manner.
Other documents that provide relevant guidance include SP 800-53 Security and Privacy Controls for Information Systems and Organizations, SP 800-30 Guide for Conducting Risk Assessments and the NIST Cybersecurity Framework.
These documents all point to several key principles that should be applied by anyone who is looking to secure robotics systems:
Defense in Depth (DiD) – Ensure that an attack would need to defeat multiple different security measures before the robot can make physical actions.
Authorization – Password policies should be developed that ensure strong passwords are created and updated regularly and default accounts are not left accessible.
Patch Management – Develop a system to prioritize security patches that might affect availability and ensure that they can be applied in a way that reduces impact.
Remote Access – Carefully audit the ways that the robotics system can be accessed without physical access to the system.
Incident Response Plans – Develop a plan on how to respond to cyberattacks against the industrial system and how to recover the system if attacks such as ransomware are successful.
Find more information at the NIST Manufacturing Extension Partnership Cybersecurity (MEP) cybersecurity resources page.
Industrial Cybersecurity at Southwest Research Institute
Southwest Research Institute engages in a wide range of activities to aid clients in securing their industrial systems. These activities include penetration tests to verify that systems are secure and that an attacker will not be able to compromise a robotics system or carry out other malicious functions. We also aid our clients in their compliance efforts, determining what steps need to be taken to bring a client in line with best practices, such as the NIST guidance mentioned above.
To learn more, contact Austin Dodson or visit SwRI’s Cyber Security Services and Intelligent Manufacturing & Process Solutions. Ryan Elder contributed to this article.

