Background
This Regular IR&D aimed to develop a comprehensive key management solution tailored to embedded systems for use in Southwest Research Institute (SwRI) cybersecurity applications. As SwRI continues to improve cybersecurity solutions, it has identified critical gaps in embedded systems where key management technology is often lacking.
Unlike traditional IT networks, embedded systems vary widely in capability and network availability, making robust key management difficult to implement. Existing embedded security solutions either bypass key management, use suboptimal methods due to resource constraints, or rely on expensive external solutions. This project sought to address these challenges by exploring open-source key management solutions used in IT networks and adapting them for the embedded space. It also examined how cryptographic hardware and embedded devices can be integrated with these key management systems.
Approach

Figure 1: Example of cryptographic key management lifecycle.
This research aimed to establish an open, scalable key management infrastructure for embedded systems with limited resources and connectivity. The system manages cryptographic keys throughout their lifecycle including provisioning, rotation, revocation, and termination (Figure 1). The research involved configuring a key management server and interface to centrally control the keys, while also developing software to enable key management operations on embedded devices.
Given the team's expertise, the automotive domain was selected as a testbed for this solution. The key management system was applied to a simulated automotive benchtop environment (Figure 2) using automotive-grade cryptographic hardware. Its functionality was validated through the use of managed keys within the Secure On-Board Communication (SecOC) protocol and an Uptane secure update implementation. X Certificate and Key Management (XCA), an open-source tool designed for internet security, was leveraged to support key creation and management.
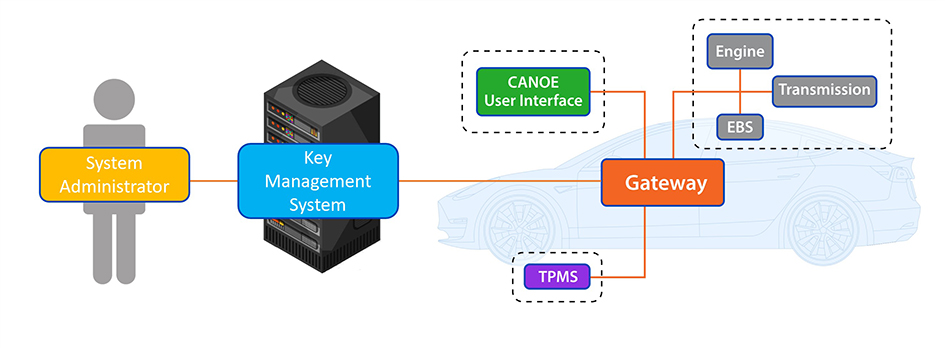
Figure 2: Simulated automotive network and key management system integration.
Accomplishments
The project successfully demonstrated the key management system’s ability to provision, replace, rotate, revoke, and terminate keys and certificates. These actions can be controlled via a graphical user interface (GUI), providing a user-friendly experience. The system’s managed keys were validated in both SecOC and Uptane applications. Additionally, the team has produced an application programming interface (API) to extend the key management system’s use to other platforms, laying the groundwork for broader cybersecurity applications in embedded systems.
