Background
The increasing reliance on satellites for infrastructure has created new prime targets for cyberattacks. Legacy satellite systems are particularly vulnerable due to their lower processing power, which constrains their ability to run conventional defensive cyber solutions. One primary threat is the hijacking of a satellite via malicious commands, allowing bad actors to remotely damage or control satellite assets. Detecting and responding swiftly to malicious commands is crucial to prevent further compromise.
Approach
The objective of this project was to design an autonomous on-board anomaly detection system capable of distinguishing malicious satellite command messages from normal ones and responding with an optimal human-in-the-loop approach. To ensure realism, a satellite was simulated using data and operational methods from a real-world spaceflight mission. The anomaly detection system was developed comprised of a command message logger, a graph-based anomaly detector, and a decision matrix. The command message logger collected and stored messages processed by the satellite’s software bus, which manages flight software tasks. Using this logged data, the system dynamically built an adjacency matrix of valid message cycles. The anomaly detector compared incoming command messages against the adjacency matrix to verify they followed a valid cycle. Messages which did not follow the expected cycle were flagged as anomalous, and their identifiers were passed to the decision matrix which referenced a table in non-volatile memory to determine the appropriate response action. The decision matrix also updated the table based on operator feedback. The system’s correctness and latency were tested by sending streams of valid and anomalous command messages through the simulated software bus.
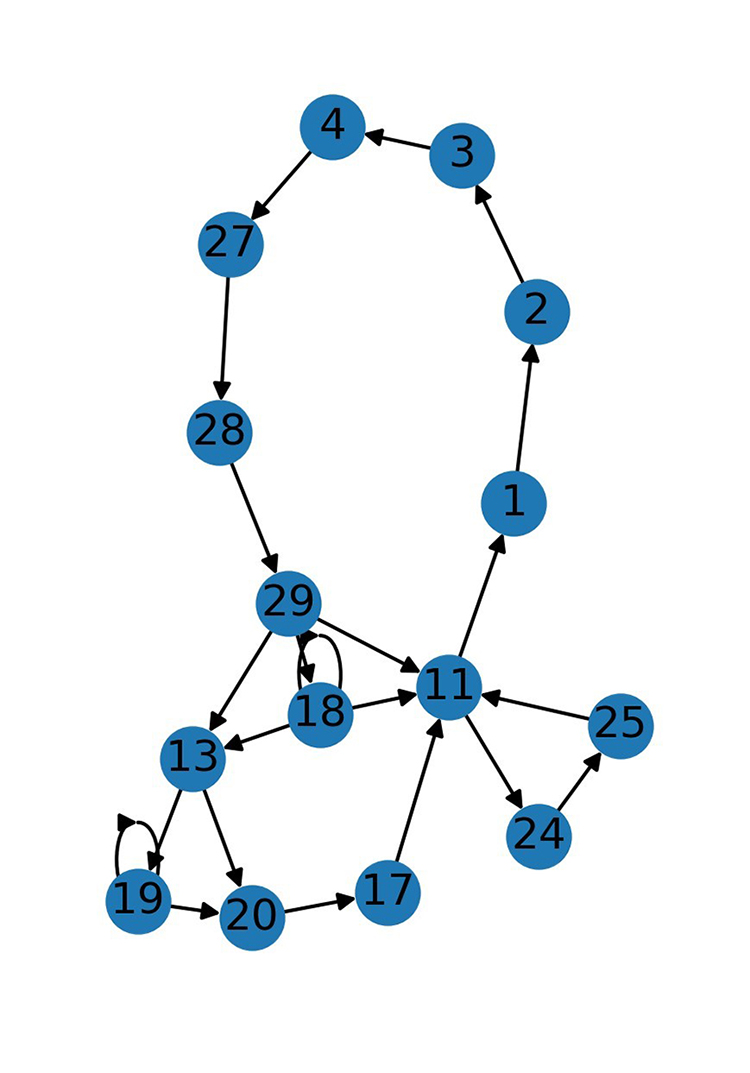
Figure 1: Command message state machine graph illustrating cycles.
Accomplishments
The system correctly identified all anomalies with a 100% success rate in every iteration of the test. The implementation of the anomaly detector resulted in a constant, O(1), lookup time achieving minimal latency. The decision matrix responded correctly to detected anomalies, and successfully updated the reference table according to operator input. The system is limited by a dependence on the accuracy of the initial dataset used to build the adjacency matrix and the inability to determine if one anomaly is more critical than another. However, the accurate and efficient performance of the system demonstrates its viability for expansion and refinement.
