SwRI engineers have developed a comprehensive cybersecurity method for vehicles. The Zero-Trust Architecture for Automotive Networks is high-level security for computerized vehicle systems, using principles proven to safeguard computers, phones and other information technology (IT) equipment. The zero-trust approach is now hitting the road, offering layers of protection against cyberthreats for vehicle electronics, software and sensors.
Listen now as SwRI Engineer and Project Leader Maggie Shipman discusses the emerging field of vehicle cybersecurity and how zero-trust architecture is advancing beyond IT applications to protect drivers.
Visit Automotive Cybersecurity to learn more about SwRI cybersecurity solutions for vehicles.
Transcript
Below is a transcript of the episode, modified for clarity.
Lisa Peña (LP): LP: You have cybersecurity measures in place for your computers, phones, and home internet routers, but what about your vehicle? Vehicle electronics sensors and software could become a target for hackers. An SwRI team is working on a comprehensive whole-system solution to protect vehicles from cyber threats. That's next on this episode of Technology Today.
[MUSIC PLAYING]
We live with technology, science, engineering, and the results of innovative research every day. Now, let's understand it better. You're listening to the Technology Today Podcast presented by Southwest Research Institute. From deep sea to deep space, we develop solutions to benefit humankind. Transcript and photos for this episode and all episodes are available at podcast.swri.org. Share the podcast and hit that subscribe button on your favorite podcast platform.
Hello, and welcome to Technology Today. I'm Lisa Peña. Tough cybersecurity for vehicles is necessary as automotive systems become more connected, relying on software and sensors to operate. The National Highway Traffic Safety Administration calls vehicle cybersecurity an exciting new and evolving field. SwRI Engineers are at the forefront of this evolution with a groundbreaking development.
Our guest today is Project Leader and SwRI Engineer Maggie Shipman joining us remotely to talk about vehicle cybersecurity and SwRI's new zero-trust architecture for automotive networks, a comprehensive vehicle cybersecurity solution. "Zero-trust" that's a key phrase in this technology. We'll learn more about what that means today. Thank you for joining us, Maggie.
[MUSIC PLAYING]
Image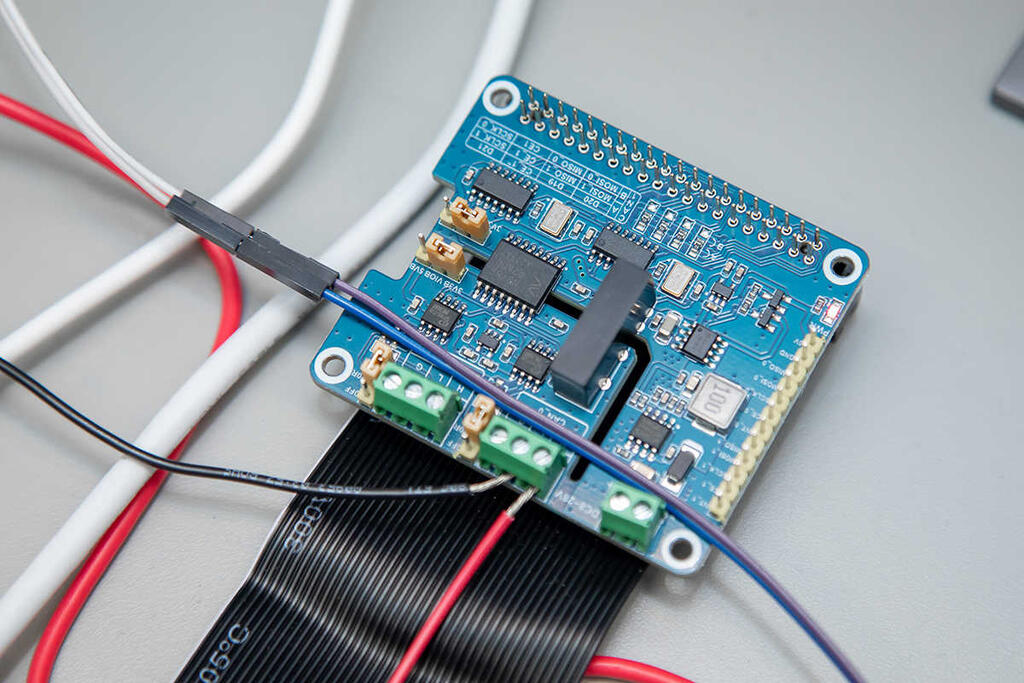
This Controller Area Network (CAN) bus interface allows developers to simulate vehicle networks to test and strengthen zero-trust automotive cybersecurity technology.
Maggie Shipman (MS): Thank you so much for having me.
LP: So Maggie, what you're sharing with us today is really insider information at this point, not widely known that this is ready for the automotive market. Your team is breaking into this fairly new field of vehicle cybersecurity with this new approach, zero-trust technology. So let's start with explaining zero-trust cybersecurity. What does that mean?
MS: Sure. So zero-trust was an originally a concept from the information technology or IT world. The whole concept really sources around the idea of never trust, always verify, and it's used to authenticate networks and assets on that network, including work computers, telephones for business, and even people.
LP: OK, so it is widely used in information technology, and you just went through some examples of how zero-trust is used in information technology in IT. Could you describe specifically how those it applications use this zero-trust technology for cybersecurity?
MS: Originally, this idea of zero-trust came about because we were trying to move away from the firewalls and the use of firewalls for network security. And so when we were using firewalls, we were really trying to keep bad actors on the outside of our networks. And so since then, we've realized that bad actors can get in those firewalls through little holes in security, and so we can't trust that no bad actors are inside our network. And so zero-trust is really about making sure that each asset is proving its identity to a root of trust and making sure that everyone who is a part of the network is supposed to be, and that can come in the form of people and employees and also their assets, like a laptop, a server, and things like that. And so a great example of seeing zero-trust in real life is all of us who use dual authentication whenever we log into our work laptops to prove our identity not by just using our password on our computer but also through a second mechanism of authentication.
LP: OK, so now, this is exciting. Your team is transferring these techniques to the automotive industry. Tell us why you want to bring zero-trust capabilities to vehicles. What was the motivation to develop this?
MS: Sure. So what we're really advocating here for is security during the design process and an overall mature cybersecurity posture for vehicle architectures. We've seen in the past that there has been not a lot of mature cybersecurity postures on vehicle architectures, and so whenever you compare the automotive industry to the dot-com boom per se, whenever that was going on, the first thought is not cybersecurity. The first thought is functionality and making sure that the system works.
And so we're in such a new phase of cybersecurity, of making sure we're advocating that this needs to be a consideration through the development of the vehicle architecture. We stepped in, and we said, zero-trust has worked great in an IT environment. And that is common through the literature even in the automotive industry at present, but no one had actually sit on it to create a publicly accessible implementation of what an automotive zero-trust architecture would look like.
LP: So are cars getting hacked? Is this a big issue? And what could a hacking scenario look like?
MS: Sure. So the quintessential automotive hack that kind of sent the creation of this automotive cybersecurity industry happened back in 2015, and all of my folks who are familiar with the automotive cyber industry know exactly what I'm talking about. And we're talking about the Jeep hack that was featured on Wired. And so two folks came in, and they were able to remotely control a Jeep with a reporter in it and were able to kill the engine of the Jeep while it was on the highway. Obviously, Jeep has come in, and they've addressed those issues. But we're still seeing issues, and so some of the most recent hacks we've seen include Tesla's electric vehicles as a target. And some researchers from the Technical University of Berlin were actually able to access additional premium features without a cost through hacking their autonomous self-driving mode that was dubbed "Elon mode."
There's some other hacks too that we've seen that also included - in 2022, some folks were able to run personal software on Hyundai vehicle infotainment, and that was kind of interesting to see because it was actually some vehicle owners who were trying to do that. And they were able to break a piece of the encryption by using key that they found online in an example from some NIST documentation. So all that to say, yes, cars are getting a hacked. It might not be something you're seeing in the civilian front, but we definitely are seeing a large range of hacks as folks who are tracking this in the industry.
LP: So at your suggestion to prepare for this episode, I did watch that Wired 2015 hack, and it is slightly terrifying. They are on the highway, and someone else is controlling their speed, their brakes. At first, it starts off innocent enough with a loud radio and windshield wipers, and it's comical. But it quickly becomes dangerous. So this is definitely something that all drivers should consider at some point as our vehicles get more and more advanced, so let's talk about that a little bit. What makes modern vehicles especially vulnerable?
MS: Sure. So when we think about it, vehicles are increasingly becoming connected to environments that are external to what you imagine when you think, "oh, my car." So we're looking at remote connections. They're now connected through Wi-Fi. You've got connection through telematics communications and even just plugging in your phone to CarPlay. We now have entered the era of incredible technology, and we're taking advantage of some really neat, neat features that we've actually created more threat vectors and a richer surface of attack.
LP: So it's definitely great that our cars can do more, but with that, we need to ramp up that security. So what does the SwRI zero-trust automotive technology system look like? How does it work to bring in that extra layer of protection?Image
SwRI Project Leader and Engineer Maggie Shipman, pictured here in a SwRI cybersecurity development lab, is leading the launch of the Institute’s zero-trust architecture for automotive networks. Her team has proven the technology, traditionally used only for IT applications, is a viable cybersecurity option for vehicles.
MS: Sure. So our vehicle architecture was developed on a vehicle communication network simulation, and so what we did was we broke out a vehicle communication network, a communication bus, and used vehicle hardware to establish a key creation and distribution method. And so when I say "keys," we're talking about encryption keys. And then we implemented several different security features that are common in the automotive industry. What was particularly interesting about our approach is that we've seen implementations of cybersecurity on some vehicles with only one of the features we've included. So some of the included features that we chose were secure boot and Secure Onboard Communication protocol from AUTOSAR. And so these two we've seen in the wild per se and being used independently from each other as a silver bullet method per se of protection. And while that's wonderful that we're moving towards implementing cybersecurity onto vehicle architectures, our position at SwRI is to continue to advocate for more. And so we also leveraged existing vehicle components, like the gateway, which you can imagine as the central hub of communication, to include intrusion detection and anomaly detection.
And so we're able to identify if there's been messages injected into the communication bus from external threat actors, and then we also are able to authenticate each piece of that bus as well. So we're going back to this whole idea of ensuring trust, and we're making each asset prove that it needs to be a part of the system continuously. And so it's a really neat concept, but what we're advocating here is not necessarily a tailored one-stop shop approach to what we've designed. We're advocating that folks in the commercial automotive industry and even the military automotive industry look at this and say, this is a holistic approach. How can I take what they've implemented and adapt it and tailor it to create this wide and rich cybersecurity posture for my specific vehicle architecture? And we're here, and we're happy to help do that.
LP: I like that you said that your new architecture is about ensuring trust because it's called zero-trust, but we want to make it clear, it's zero-trust in, as you said, the bad actors out there, not trusting anything that comes into the network from the outside. So can you talk about that name a little bit? Maybe does it cause some roadblocks for you?
MS: Sure. There's definitely some irony in the name right. We're engineers. We're not publicists. So that's kind of funny. But the whole idea of zero-trust really comes from assuming zero trust within a network, and so within our network we're considering, obviously, is the vehicle. But we're assuming that each asset on the network may or may not be supposed to be there, and that's where that zero-trust piece comes in.
It's interesting because it definitely has become a buzzword within the industry. I've noticed sometimes you bring up zero-trust, and people genuinely make a face like they need to spit something out. So you have to tailor your conversations to folks because really what we're advocating for is a secure vehicle architecture and a mature cybersecurity posture for all vehicles on the road.
LP: Right. OK, so we understand the name a little better now. Are there currently other cybersecurity systems in use for vehicles? Why do you see the zero-trust option as a better approach?
MS: Sure. So we definitely have seen pieces of cybersecurity in different vehicles. Zero-trust I personally think is a better approach because it's not just a single security feature that's being added after the fact. What's pretty common in the industry right now is because security is genuinely an afterthought, its implementation is occurring after development, and so what we've seen is systems that have been patched per se after they've been developed, which is really not the best practice of how to apply cybersecurity to a system right.
And so through zero-trust, you're having to accommodate the concept of zero-trust at the beginning decisions of design and Development of the vehicle architecture, and so we're advocating here for a holistic approach that is considered throughout the entire design life cycle. And I think that's really what makes zero-trust a better option, because you're able to incorporate those components that we've seen successful as one solution in vehicles, and you're able to add more. And so it's really creating this robust system of security that previously wasn't there.
LP: All right. And this isn't just a cybersecurity theory, a theoretical system, so to speak. You have researched it. You've developed it, and you've even tested it. How has the system been tested?
MS: Sure. So the interesting part about this is that we're in a resource-constrained environment, which I think goes kind of unnoticed typically, but let me elaborate a little bit on that. So the part that is particularly interesting is that you think of an IT network, and you have all the computational power in the world at your fingertips. If you need more speed, you go buy more equipment. You upgrade it you. Have the room built out so you have more room. That's not the case for vehicles, and so what we're looking at here is applying these very complex security solutions that require algorithms and encryption in some cases to ensure authentication. And with that comes a need for more computational power, and so if you turn your computer on and it lags for a few seconds while it boots up, that's not a significant issue. That's not a risk to your safety.
But if you're sitting in your vehicle and, all of a sudden, you have your vehicle lagging because it can't keep up with the demands on its resources and, all of a sudden, your brakes don't work in real time, that's a safety-critical issue. So a lot of our testing around this project has really looked at whether or not we can accommodate these security solutions with minimal disruption to the functionality of the vehicle. We've been able to achieve pretty good timing situations here, pretty good execution times. We're looking at latency at startup. Does the vehicle turn on when it needs to? Is it seeing that lag? And we've been able to get some pretty good numbers. On top of that, you have to be able to detect any erroneous or bad messages 100% of the time through anomaly detection or it's just not worth it, and we have achieved that number. So I would say our testing overall has gone incredibly well. We are seeing a move in the future towards hardware accelerators and increased computational power, and with that only opens up more opportunity to include more security solutions.
LP: All right. So you have explained how zero-trust originated for it applications outside of automotive, but has this been done before using those zero-trust capabilities for vehicles?
MS: Sure. So zero-trust has been certainly talked about throughout the industry. To my knowledge, ours is going to be the first public implementation that folks in the industry will be able to read about, dive into, and really digest. We are planning to publish our paper through some conferences and really garner up more discussions around how we implemented it. Obviously, like I said, there's been pieces of this architecture that have been done, but the interesting piece about ours is that we're able to achieve all of it with minimal disruption.
LP: So working on this solution, what do you think needs to change about how we think about cybersecurity for vehicles? We hear about cybersecurity for just about everything, but it's not cybersecurity for vehicles I don't think is at the forefront. So what do you think needs to change?
MS: I honestly think our perception needs to change. Vehicles are very much computers just as much as your cell phone is or your laptop is, and I think it's time we start treating them as such and as assets that we should be protecting.
LP: And what type of vehicles do you think this particular zero-trust system would work best with?
MS: Sure. So from our point of view, this is a highly tailorable solution, and it can be fit to any type of vehicle or vehicle architecture. I personally believe that it has applications in the commercial and military space.
LP: Wow, so even, as you just said, military vehicles could benefit from this level of security, and that's also really neat that a car I drive could also have that same level of protection that would be offered to, let's say, a military vehicle. So you envision this cybersecurity system being part of the vehicle's design from the manufacturer rather than installed after the car is built. Why is being baked into the design, so to speak, a better option, and any challenges to introducing this zero-trust approach to vehicle manufacturers to have them put it in during the design phase?
MS: Sure, sure. So I think I've kind of been hitting this point home, but considering cybersecurity at the beginning is truly key. I think if we look at applying cybersecurity after the fact, not just from a zero-trust perspective, but if you think of automotive cybersecurity as a whole, those solutions just aren't going to be very strong. I think that if you allow yourselves time and budget to accommodate these cybersecurity needs that go along with these solutions at the beginning of the design process, you're able to achieve a more mature posture.
And I think there definitely has been some challenges. Obviously, we're still advocating for that, so we're not seeing that widely across the industry. There are definitely some folks who are doing that and are implementing cybersecurity at the beginning of that design process, but that also it requires time. It requires money, and it requires expertise. And I think SwRI offers expertise that can certainly assist in that process.
LP: So I want to make sure we cover this before we move on through the podcast, but I really want to understand SwRI's approach. So is our zero-trust system several layers you mentioned a secure boot and some communication protocol security. What are how can I visualize what we're talking about when we are talking about the system as a whole?
MS: Sure. So I think the best way to visualize this system is if you think of a sprawling network and just almost a bunch of assets, a bunch of blocks connected through a communication network, and almost as if you were I was holding a can and you were holding a can and we had a string from one to the other. And in order to communicate, you are yelling down the line, and I can hear you on the end. And so there's not a lot of security there, and that's kind of what we're looking at with a very basic vehicle communication bus. And so we are building on top of that vehicle architecture all of these security features. And so to go down the line, we are implementing secure boot, like you mentioned, and secure boot is authenticating the pieces of software on each of these cans that we're holding or each of these assets.
And every time it goes to run that software at the beginning of the vehicle turning on, it has to authenticate itself. It has to prove itself. That way, we can prove that that software has not been tampered with since the last time that the system was booted. And so we are achieving that 100% of the time. On top of that, we're doing message authentication through the Secure Onboard Communication protocol, and so this is kind of a commonly used protocol from AUTOSAR. The interesting thing about this protocol is that there's a lot of room to make implementations different from others. So there's a general guidance, but the way you implement it can be different.
SwRI has looked at it, and we've created an implementation within the protocol that we believe is secure. And we've set it up, and we can offer assistance to others who are looking to set it up as well. And so through that, we're able to authenticate the messages that go down the line, and so that means that whatever I yell into the can, we're proving that's actually what I yelled. And you're hearing the truthful, honest message that I sent across the line. On top of that, we are looking at monitoring system accuracy, and so we have an anomaly detection system that identifies 100% of illicit packets on the network. And so what that looks like is if you have a sneaky bad actor and they come in and they try to pretend like they're me and they put their own message on the line and they yell down the line and you're trying to receive that message and you're like, oh, that's interesting, Maggie just sent me one, well, we're able to tell you on the spot, no, that message did not come from Maggie.
And that's huge because that's what we're looking at with some of these hacks. If a bad actor comes in and they inject a message on the line and it says "slam on the brakes" when she's going 80 miles an hour down the highway, probably not a great idea. And so there's some other aspects that we're implementing too, but those are kind of the big ones. And so I guess a great visualization is just that this entire approach is building off of a very open network per se, and we're adding layers and layers of security that ultimately make the experience for everyone related to the system more secure. And you can enjoy that functionality without worrying about if it's been tampered with.
LP: Thank you for that excellent can-to-can description because I really got it. It's like that message going from can to can and there are these blocks hitting that message to make sure that message is what it says it is, sounds like it should. So that can translate to our vehicles, that the information it's receiving is beneficial to the driver, is what the driver needs rather than someone coming in from the outside and putting it there, so.
MS: Well, the cool thing about that little analogy is the communication network I've actually been talking about is a controller area network. It's actually called the CAN bus, so there's a little engineering humor there too.
LP: [LAUGHS] OK, perfect, double cool. OK, so if vehicle manufacturers include this new level of cybersecurity, will this make vehicles more expensive for drivers?
MS: So yes and no. So I think there's some different ways to go about achieving this. It really is going to be the extent in which they apply the zero-trust architecture. We've seen obviously, we're asking for a holistic approach. We're advocating for a holistic approach, but if vehicle manufacturers choose to incorporate one piece first and another piece down the line, I'm not sure that there would be an incredible raise of cost to the consumer there. I also think that you could take advantage of some of the hardware that's on the vehicle and look at leveraging that to accommodate some of these demands for resources from the security features.
We also are looking towards the future, and hardware accelerators are a hot topic. And so when I say "hardware accelerators," it's very much what it sounds like in the mundane sense is that you're including more hardware that is able to speed up this computational. So if we're having to encrypt keys, distribute keys, do these complex mathematic calculations as a component of implementing these security features, hardware accelerators are going to be able to speed up that process for us. And so I think it really comes down to how the commercial manufacturer or military vehicle company is looking at implementing this solution. Where along the timeline are they looking to implement it? Are they going to leverage existing hardware? Are they going to include new hardware? It definitely there's not a simple answer, but I don't think it's going to have much disruption to the average consumer.
LP: And where are you right now in talks with manufacturers to implement this type of technology?
MS: Sure. So we've talked to some folks. We're really advocating; I'll go back to it. If you're just looking at implementing a piece and zero-trust or secure vehicle architecture is the end goal that's on the horizon, and we're working to get there. I don't think we've seen folks approach this from, we're going to do everything right now and do it all right now in this one go and accommodate everything, because that's just not really how change works.
They're going to take it piecemeal. They're going to look at how it suits their system, and they're going to roll it out when it's ready because there's a lot of risk associated with development across the board for anything, and especially in safety-critical components, you want to be sure that what you're adding and handing to the consumer is 100% functional. And we believe that the software that we've developed definitely can be handed off and work to get the vehicle manufacturer to that position.
LP: What do you see long term for this technology, and how soon could we see it installed in vehicles?
MS: Sure. So long term, I think that we're going to continue to tailor the zero-trust approach. This is not a one-size-fits-all solution. This is something that needs to be tailored to each vehicle, and I think as security features progress and continue to be developed, you'll see different features added to this architecture. And I think what we're leveraging here is the idea that you're setting the groundwork, you're setting the architecture, you're setting the framework that allows you to have easy portability to add cybersecurity features later down the line. And I think that's really what makes this incredibly cool is that you're setting yourself up for success in the long run.
So I think ideally we'll see some of this turn around in the next several years. I think we've seen an increase in cybersecurity from several folks, but again, I think the big shift is going to come whenever we see across the automotive industry that people are beginning to consider cybersecurity at the beginning of the design phase.
LP: What kind of response are you getting right now when you reach out to these automotive contacts, saying, hey, look, this is what we have going on here? What has been the reaction thus far?
MS: Sure. I think we're getting to a point now where we have folks definitely recognizing that there is a need, and it is such an incredibly new industry. 2015 we're not even really 10 years old yet. And to see the speed at which people have recognized that this is a problem and let's try to solve it is really cool.
I think that we've had some folks turn their nose up at the idea of a full implementation just because they're worried about cost, but we're starting to get to those people. I think ideally, once you get talking to the right folks, there is excitement there, and everyone at the end of the day wants to ensure that the consumer, the public, the community is safe when they're driving down the road.
LP: All right, Maggie, a lot of great information today. But we also like to get to know the person behind the technology so have to ask you, what was your path to cybersecurity? And any advice for someone interested in breaking into the field?
MS: Sure, so I'm relatively new to cybersecurity, but I'm not new to STEM. So I was the girl who grew up doing the robotics competitions. That was "build the robot from LEGOs." And then I actually traveled to San Antonio for one of the first times from Dallas, where I grew up, in the Fort Worth area, down for the State Science Fair, thought I was really cool. And then in college, I contributed on the board for some hackathons at Auburn and ultimately graduated with my degree in computer engineering from Auburn in 2022.
LP: And what is it about cybersecurity that really sparks your interest?
MS: Honestly, I came into my interview at SwRI obviously right out of school, and I think the best way I just could describe my quintessential response that I think, looking back, got me into this field was I just really frankly told my interviewer that I liked breaking stuff.
LP: [LAUGHS] We find that a lot with our engineers, yeah.
MS: It's a fun time. And he looked at me, and he goes, great. That's what we do every day. You'd really like it here. And so I was headed back up to Auburn. I was flying out of the San Antonio Airport, and I get a call from my then-manager, Vic Murray. And he's like, you want to come down here and break some stuff every day?
LP: [LAUGHS]
MS: And I was like, yeah, that sounds great, so.
LP: And here you are, breaking stuff, breaking into new things, ground-breaking research and development. It's all part of the same package here at SwRI, right?
MS: Absolutely, absolutely.
LP: So what is your advice for someone interested in this field?
MS: Sure. So I actually take a lot of pride in reaching out to folks who are interested in this area. I like to I find a lot of joy in giving back to some of the communities that I participated in when I was younger. So I helped out with the local San Antonio Robotics. They've got the kids in middle school and high school doing the competitions with their robots, which is what I did there age.
And then just getting connected and plugged in. I just joined this Women's Cybersecurity Security Alliance that pairs young women with mentors, and so it's just opportunities like that. Look out for people. Get your hands on some cool stuff. Try it out. And, I think, don't be afraid to break something, do it wrong because nine times out of 10, everybody around you has done it wrong at least five times before that. And that's what I've learned. It's never a situation where questions are not welcome, and I think once you find that confidence a lot of doors are going to open up for you.
LP: So much great advice, so much great information today. Maggie that likes to break things, your team is leading the way in vehicle cybersecurity with the zero-trust architecture for automotive networks, really such a critical technology that we may see on board many vehicles soon from the cars we drive daily to the military vehicles you were describing. So Maggie, again, thank you for being here today to tell us all about it.
MS: Absolutely. Thanks for having me. I enjoyed it.
And thank you to our listeners for learning along with us today. You can hear all of our Technology Today episodes, and see photos, and complete transcripts at podcast.swri.org. Remember to share our podcast and subscribe on your favorite podcast platform.
Want to see what else we're up to? Connect with Southwest Research Institute on Facebook, Instagram, Twitter, LinkedIn, and YouTube. Check out the Technology Today Magazine at technologytoday.swri.org. And now is a great time to become an SwRI problem solver. Visit our career page at SwRI.jobs.
Ian McKinney and Bryan Ortiz are the podcast audio engineers and editors. And sometimes, co-host. I am producer and host, Lisa Peña.
Thanks for listening.
[MUSIC PLAYING]
Southwest Research Institute helps the automotive industry develop the latest cybersecurity solutions for passenger vehicles. We work with clients to help improve the automotive cybersecurity of their systems. As an independent, not-for-profit company, SwRI provides guidance to align with key automotive standards.
How to Listen
Listen on Apple Podcasts, or via the SoundCloud media player above.
